Network: Difference between revisions
Emoji & image fix |
|||
| (11 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
👻 This page should document some bits of the network infrastructure of Kanthaus. Please maintain so people with a bit of network knowledge can understand and maintain the network. | 👻 This page should document some bits of the network infrastructure of Kanthaus. Please maintain so people with a bit of network knowledge can understand and maintain the network. See also [[Server]]. | ||
== Overview == | == Overview == | ||
| Line 6: | Line 6: | ||
raw file for modifying: /images/network-topology.svg | raw file for modifying: /images/network-topology.svg | ||
--> | --> | ||
== ISP == | |||
We currently use Telekom as our internet provider. They have a [https://www.telekom.de/hilfe/hilfe-bei-stoerungen/leitungspruefung help page] for diagnosing internet issues from their side: good idea to check this first if the wifi networks are still up, but not connected to the internet. | |||
== TRUNK network == | == TRUNK network == | ||
| Line 134: | Line 138: | ||
| K20-0 hallway | | K20-0 hallway | ||
| Archer C5 v1.2 | | Archer C5 v1.2 | ||
| | |switch with servers | ||
|- | |- | ||
| AP | | AP | ||
| Line 141: | Line 145: | ||
| K20-1 hallway | | K20-1 hallway | ||
| Archer C5 v1.2 | | Archer C5 v1.2 | ||
| | |maybe overloaded | ||
|- | |- | ||
| AP | | AP | ||
| Line 155: | Line 159: | ||
| K20-B water room | | K20-B water room | ||
| Archer C5 v1.2 | | Archer C5 v1.2 | ||
| | |for IoT devices | ||
|- | |- | ||
| AP | | AP | ||
| <code>dragon-k22- | | <code><s>dragon-k22-1</s></code> ? | ||
| 192.168.178. | | <s>192.168.178.202</s> 192.168.178.217 | ||
| K22- | | K22-1 hallway | ||
| Archer C5 v1.2 | | Archer C5 v1.2 | ||
| | |Timber installed the "normal" firmware, now it has a separate wifi (see [https://chat.kanthaus.online/kanthaus/pl/px368istkib7xdf4ekae76oqze Mattermost]) | ||
|- | |- | ||
| AP | | AP | ||
| Line 176: | Line 173: | ||
| K22-2 hallway | | K22-2 hallway | ||
| Archer C5 v1.2 | | Archer C5 v1.2 | ||
| | |maybe overloaded | ||
|- | |- | ||
| Managed Switch | | Managed Switch | ||
| Line 247: | Line 230: | ||
| ESP32-CAM | | ESP32-CAM | ||
| see [https://git.kanthaus.online/kanthaus/door-esp32 docs] | | see [https://git.kanthaus.online/kanthaus/door-esp32 docs] | ||
|- | |||
| radiator fan switch | |||
| <code>socket-radiator-fansipan</code> | |||
| 192.168.5.41 | |||
| Fansipan | |||
| LSPA9/CB2S/BK7231N | |||
| | |||
|- | |||
| radiator fan switch | |||
| <code>socket-radiator-elephant</code> | |||
| 192.168.5.42 | |||
| Elephant Room | |||
| LSPA9/CB2S/BK7231N | |||
| | |||
|- | |||
|electricity monitor | |||
|<code>socket-2-k22-3-aircon</code> | |||
|192.168.5.43 | |||
|K22-3 | |||
|LSPA9/CB2S/BK7231N | |||
| | |||
|} | |} | ||
| Line 287: | Line 291: | ||
=== Building customized OpenWRT for Archer C5 === | === Building customized OpenWRT for Archer C5 === | ||
<pre> | |||
< | ssh kanthaus-server | ||
sudo -iu openwrt-builder | |||
cd openwrt | |||
make | |||
ls -l bin/targets/ath79/generic/ | |||
</pre> | |||
==== included changes ==== | ==== included changes ==== | ||
| Line 314: | Line 315: | ||
Documentation: https://openwrt.org/docs/guide-developer/toolchain/use-buildsystem | Documentation: https://openwrt.org/docs/guide-developer/toolchain/use-buildsystem | ||
ssh kanthaus-server | |||
sudo -iu openwrt-builder | |||
sudo -iu openwrt-builder | cd openwrt | ||
cd openwrt | git pull | ||
git pull | git checkout v23.05.2 | ||
git checkout v23.05.2 | |||
Edit <code>feeds.conf</code> to change the branch for each feed to the new version, e.g. <code>...;openwrt-23.05</code> | Edit <code>feeds.conf</code> to change the branch for each feed to the new version, e.g. <code>...;openwrt-23.05</code> | ||
./scripts/feeds update -a | |||
./scripts/feeds install -a | |||
./scripts/feeds install -a | make -j4 defconfig download clean world | ||
make -j4 defconfig download clean world | ls -l bin/targets/ath79/generic/ | ||
ls -l bin/targets/ath79/generic/ | |||
Errors during <code>make world</code> are to be expected, usually the set of default packages changed and dependency conflicts are happening. Investigate generated the <code>.config</code> file and compare with the official ones at https://downloads.openwrt.org/releases/23.05.2/targets/ath79/generic/config.buildinfo | Errors during <code>make world</code> are to be expected, usually the set of default packages changed and dependency conflicts are happening. Investigate generated the <code>.config</code> file and compare with the official ones at https://downloads.openwrt.org/releases/23.05.2/targets/ath79/generic/config.buildinfo | ||
| Line 344: | Line 343: | ||
# Perform any last updates from the web UI. | # Perform any last updates from the web UI. | ||
# Delete the configuration backup again, it can contain secrets. | # Delete the configuration backup again, it can contain secrets. | ||
# Check if <code>os-realtek-re</code> is installed | |||
# Check if VPN for kanthaus-gast is online | |||
=== Pitfalls === | === Pitfalls === | ||
Latest revision as of 12:38, 30 November 2025
👻 This page should document some bits of the network infrastructure of Kanthaus. Please maintain so people with a bit of network knowledge can understand and maintain the network. See also Server.
Overview
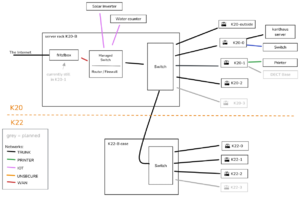
ISP
We currently use Telekom as our internet provider. They have a help page for diagnosing internet issues from their side: good idea to check this first if the wifi networks are still up, but not connected to the internet.
TRUNK network
the backbone of our network, connecting all Access Points and the central firewall, carries all the different networks via VLAN:
| VLAN-ID | IP Range | Name | Purpose / Devices |
|---|---|---|---|
| untagged | 192.168.178.x | ADMIN | configuration tnterfaces of all AP’s & Switches |
| 4 | 192.168.4.x | PRINTER | connection between print server (kanthaus-server) and printer |
| 5 | 192.168.5.x | IOT (former SMA) | only access to kanthaus-server and potentially whitelisted internet IP’s + isolated clients¹ |
| 100 | 192.168.100.x | RESTRICTED | normal internet access + isolated clients¹ |
| 101 | 192.168.101.x | VPN | tunneled to VPN (currently NL) |
| 102 | 192.168.102.x | UNSECURE | normal internet access |
¹ client isolation does not work between LAN <-> LAN clients
Wifis
| SSID | Network | Encrypt. | 802.11r | 802.11w | Isolation | Comment |
|---|---|---|---|---|---|---|
kanthaus
|
RESTRICTED | WPA3 | -¹ | required | on | |
kanthaus-insecure
|
INSECURE | WPA2 | - | - | - | unsupported drivers, LAN parties, etc. |
kanthaus-gast
|
VPN | - | - | - | on | |
kh-admin
|
ADMIN | WPA3 | - | required | - | |
kh-iot
|
IOT | WPA2 | - | - | on |
802.11r: Fast Roaming 802.11w: Management Frame Protection
¹ would be cool to have it on, but eventually led to issues. let’s reevaluate in a few months
Device list
| Type | Name | Admin-IP | Location | Hardware | Comments |
|---|---|---|---|---|---|
| Router | fritz.box
|
192.168.200.1 | K20-1 hallway | FritzBox 7530 | DSL termination (on main network), telephone |
| Router | firewall
|
192.168.178.1 | K20-B rack | central router / firewall | |
| AP | dragon-k20-0
|
192.168.178.207 | K20-0 hallway | Archer C5 v1.2 | switch with servers |
| AP | dragon-k20-1
|
192.168.178.201 | K20-1 hallway | Archer C5 v1.2 | maybe overloaded |
| AP | dragon-k20-3
|
192.168.178.208 | K20-3 center | Archer C5 v1.2 | |
| AP | dragon-k20-B
|
192.168.178.206 | K20-B water room | Archer C5 v1.2 | for IoT devices |
| AP | |
K22-1 hallway | Archer C5 v1.2 | Timber installed the "normal" firmware, now it has a separate wifi (see Mattermost) | |
| AP | dragon-k22-2
|
192.168.178.203 | K22-2 hallway | Archer C5 v1.2 | maybe overloaded |
| Managed Switch | k20 firewall switch | 192.168.178.9 | K20-B rack | TL-SG108E | |
| Managed Switch | k22 trunk switch | 192.168.178.10 | K22-B stairs | GS108E v3 | |
| Switch | k20 trunk switch | - | K20-B Rack | provides PoE for some AP’s in K20 | |
| Server | kanthaus-server
|
192.168.*.2 | K20-0 hallway | Server, i5-2500K, 16GB Ram | file storage, nextcloud, foodsharing gitlab CI Server, housebus logging & time/sunset provider (see Repo) |
| Main water meter reader | mainwatermeter
|
192.168.5.37 | K20 basement (former heating room) | ESP32-CAM | see [[./water.html|Water usage tracking]] |
| Warm water meter reader | warmwatermeter
|
192.168.5.38 | K20 basement (rainwater room) | ESP32-CAM | see [[./water.html|Water usage tracking]] |
| Ventilation watcher | ventilation
|
192.168.5.39 | K20 attic | ESP32-WROOM | see docs |
| K20 door | k20-door
|
192.168.5.40 | K20 hallway | ESP32-CAM | see docs |
| radiator fan switch | socket-radiator-fansipan
|
192.168.5.41 | Fansipan | LSPA9/CB2S/BK7231N | |
| radiator fan switch | socket-radiator-elephant
|
192.168.5.42 | Elephant Room | LSPA9/CB2S/BK7231N | |
| electricity monitor | socket-2-k22-3-aircon
|
192.168.5.43 | K22-3 | LSPA9/CB2S/BK7231N |
Firewall / Router
Central point of all subnets, routes between them
- runs OPNSense
- due to lack of ports on firewall, a VLAN switch added, bound to the firewall, also connecting to the fritz!box
- Features:
- VPN client
- DNS Server
- DHCP Server
Access Points
- see Device list
- so far all Archer C5 v1.2
- centrally configured by OpenWISP: https://openwisp.im.kanthaus.online (only reachable inside the
ADMINnet) - starting point for other ethernet cables on that floor
- in K20 all powered by PoE (802.3af) from the switch in the basement
Printer (Canon C2025i)
- Printer is in its own subnet together with the kanthaus-server
- On the kanthaus-server, there is CUPS running with printer sharing and auto discovery in the networks via avahi-daemon
- In
RESTRICTEDandUNSECUREthe printer is also reachable directly via 192.168.4.153:9100
kanthaus-server
- Most of the services are running inside a docker-compose setup
- Repo: https://git.kanthaus.online/kanthaus/kanthaus-server-services
- in
/opt/kh-services - checking state:
docker-compose ps - starting everything:
docker-compose up -d - logs:
docker-compose logs -f --tail=20
- BTRFS raid for HDD’s under
/data
Random notes
Building customized OpenWRT for Archer C5
ssh kanthaus-server sudo -iu openwrt-builder cd openwrt make ls -l bin/targets/ath79/generic/
included changes
- root password
- default IP
192.168.178.200in ADMIN range - switch: all ports in ADMIN net
- disabled DNS rebind protection
- wireless interface names
- additional packages
- openwisp-config
- prometheus-node-exporter-lu
- luci-ssl (for https)
- ebtables (for effective client isolation)
- tcpdump (for easier debugging)
Upgrading customized OpenWRT
Documentation: https://openwrt.org/docs/guide-developer/toolchain/use-buildsystem
ssh kanthaus-server sudo -iu openwrt-builder cd openwrt git pull git checkout v23.05.2
Edit feeds.conf to change the branch for each feed to the new version, e.g. ...;openwrt-23.05
./scripts/feeds update -a ./scripts/feeds install -a make -j4 defconfig download clean world ls -l bin/targets/ath79/generic/
Errors during make world are to be expected, usually the set of default packages changed and dependency conflicts are happening. Investigate generated the .config file and compare with the official ones at https://downloads.openwrt.org/releases/23.05.2/targets/ath79/generic/config.buildinfo
How to update OPNsense
There is a short downtime involved during the two reboots, usually 2 minutes each.
- Join the
kanthaus-adminwifi network and log in to 192.168.178.1 (userroot, password in keepass). Export the configuration to make a backup. - Check if updates are available (System->Firmware->Updates)
- In case of minor updates, just use the button to perform
- If there is a major update (2x per year), download the newest version from https://opnsense.org/download/, unzip and flash to any USB stick
- Take a VGA monitor, a USB keyboard and the USB stick to the K20 basement big room, open the rack box and connect the devices to the small computer (HP)
- Log in with the USB keyboard (same credentials as above) and trigger a reboot. It should now boot from the USB stick.
- Press any key when it prompts to run the “Importer”. Now it will boot up a live environment and read the configuration file. If successful, network services should run as before.
- If all looks good, it’s time to install to disk. Run
opnsense-installerfrom the shell (either on local keyboard or via ssh), choose ZFS and let the installer do its job. - Remove the USB stick and reboot again.
- Check if the system came up good.
- Perform any last updates from the web UI.
- Delete the configuration backup again, it can contain secrets.
- Check if
os-realtek-reis installed - Check if VPN for kanthaus-gast is online
Pitfalls
- We use 802.1q VLAN tagging. All switches everywhere need to have at least passive passthrough support, otherwise the Vlans disappear at that switch. I don’t know of any gigabit switch that does not support this.
- Again Vlan: Managed switches normally need to have all VLANs that should be forwarded (also tagged -> tagged forward) defined in them.
- Again Vlan: Some Access Points like WDR841 v7/v8 cannot handle tagged and untagged vlan on the same port at the same time. So far, we don’t have any equipment like that and likely we will never have, but just to know…
- Again Vlan: fritz boxes have their switch in managed vlan mode and don’t forward any tagged vlan